- cross-posted to:
- privacy@lemmy.ml
- technology@lemmy.world
- cross-posted to:
- privacy@lemmy.ml
- technology@lemmy.world
Malicious code planted in xz Utils has been circulating for more than a month.
In some cases, the backdoor has been unable to work as intended. The build environment on Fedora 40, for example, contains incompatibilities that prevent the injection from correctly occurring.
It’s really funny that it’s package incompatibilites that saved us.
There’s a joke that I can’t find now about how hard it is to install a virus in Linux even if you try.
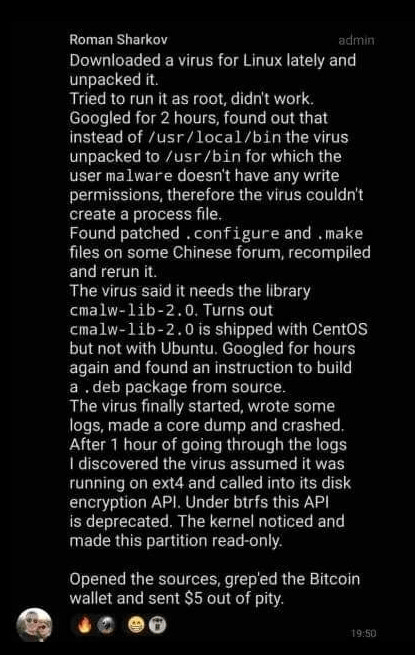
That’s it! Thank you!
Transcription:
Downloaded a virus for Linux lately and unpacked it.
Tried to run as root, didn’t work.
Googled for 2 hours, found out that instead of
/usr/local/binthe virus unpacked to/usr/binfor which the usermalwaredoesn’t have any write permissions, therefore the virus couldn’t create a process file.Found patched
.configureand.makefiles on some Chinese forum, recompiled and rerun it.The virus said it needs the library
cmalw-lib-2.0. Turns outcmalw-lib-2.0is shipped with CentOS but not with Ubuntu. Googled for hours again and found an instruction to build a.debpackage from source.The virus finally started, wrote some logs, made a core dump and crashed. After 1 hour of going through the logs I discovered the virus assumed it was running on ext4 and called into its disk encryption API. Under btrfs this API is deprecated. The kernel noticed and made this partition read-only.
Opened the sources, grep’ed the Bitcoin wallet and set $5 out of pity.
You know how “the most stable ABI on Linux is win32”? I wonder if there are already win32 viruses targeted at linux, shipped in cracked games for example.
It’s looking more and more like this was a Chinese state-sponsored operation.
https://boehs.org/node/everything-i-know-about-the-xz-backdoor
Nothing will come about from it, except for a couple people saying, “Oh, you!” to China.
That was an interesting rabbit hole to delve into, thanks.
Gotta love debian stable.





