So I got Fairphone 4, with /e/ os, a couple of days ago. When I connected it to my NextDNS I saw that it was trying to connect to some weird addresses, like every 5-10 minutes. I searched Internet a bit and found out that it was something with snapdragon cpu and location services. I travel a lot and use Organic Maps for navigation, so location was enabled almost all day on the phone. I turned off location services and connections stopped, and everything was fine for a couple of days.
Today I came home, checked logs in NextDNS and saw that phone started doing the same connections almost constantly even with location turned off.
Can I do something about this, other than allowing these connections? These connections are probably so numerous because they are getting blocked. If I allowed them, phone would maybe call home once in a couple of hours. I would rather not allow them, but I don’t want 20% of battery to be eaten by this.
I found a few links summarising this:
- https://old.reddit.com/r/nextdns/comments/14919dp/randomly_pathnxtracloudnet_is_stopped_getting/jo5n5va/
-
It’s Qualcomm’s URL for downloading assisted GPS almanac days
-
- https://teddit.net/r/privacy/comments/12yii9u/comment/jhojlr7/
- Graphene OS’ relevant documentation: https://grapheneos.org/faq#default-connections
On 4th and 5th generation Pixels (which use a Qualcomm baseband providing cellular, Wi-Fi, Bluetooth and GNSS in separate sandboxes), almanacs are downloaded from
https://qualcomm.psds.grapheneos.org/xtra3Mgrbeji.binwhich is a cache of Qualcomm’s data. Alternatively, the standard servers can be enabled in the Settings app which will usehttps://path1.xtracloud.net/xtra3Mgrbeji.bin,https://path2.xtracloud.net/xtra3Mgrbeji.binandhttps://path3.xtracloud.net/xtra3Mgrbeji.bin. GrapheneOS improves the privacy of Qualcomm PSDS (XTRA) by removing the User-Agent header normally containing an SoC serial number (unique hardware identifier), random ID and information on the phone including manufacturer, brand and model. We also always fetch the most complete XTRA database variant (xtra3Mgrbeji.bin) instead of model/carrier/region dependent variants to avoid leaking a small amount of information based on the database variant.Note sure if e/OS/ has taken as much care as Graphene has to make the requests more private. Then again, they don’t claim to be the most private OS, just De-Googled.
Edit: this is also a good read for further attempts to make your device more private: https://grapheneos.org/faq#other-connections
Android is so troublesome, I am tempted to just install Ubuntu Touch and be done with this.
I have a linux phone on the shelf, because in real life I need apps that are only available on android …
Which apps?
Banking, usable gps navigation with live traffic, workout tracker that can read and log gps and data from my Polar H10 and smartwatch.
I use online banking and Garmin smartwatch so when Linux phone becomes mainstream, I don’t be locked down
plus it looks like WhatsApp is getting interoperability and we may see a semi open source Linux client
For me, it’s something to use a Mi Band and banking apps. The rest would probably be doable on GNU phone as well.
(I only said “GNU”, since both operating systems already use the Linux kernel.)
deleted by creator
Ah, it’s just a quirk of e/OS/. Nothing much - and you can run a DNS filter on your mobile to get rid of this problem (Bonus: won’t take too much of battery since it’ll not be operating a VPN since you’re root)!
I haven’t heard much about Ubuntu Touch - does it work well?
I am kind of new to all these privacy things. So what do you exactly mean by getting rid of this problem? I have DNS which blocks these connections but phone is still making them. How can I make the phone stop doing that?
Ubuntu Touch is just a linux distro for your phone. I actually haven’t used it yet, but according to their website, the Fairphone 4 has really good support. So I might try it.
Ah, I didn’t manage to recollect your mention of NextDNS in your post. There’s no need to change anything regarding your DNS settings in such a case; it won’t take much of your battery.
Here’s a related discussion on the /e/OS forum: https://community.e.foundation/t/qualcomm-chipsets-data-collection-linked-to-the-a-gps-service-in-e-os/48982. Note that the domain mentioned in the discussion is
izatcloud.net, however, for your purposes you can consider it the same as the domains you’re seeing.What can /e/OS do?
The SUPL-A/GPS case is well-know for a long time. Though it’s probably a low impact case in term of user’s privacy, we are evaluating how to prevent or mitigate it in /e/OS.
Options we have today:
- Block SUPL requests using /e/OS’ Advanced Privacy tracker control. But that would probably kill the A/GPS service, making the GPS location service very, very slow.
- Proxy SUPL requests to anonymize their originr. That’s an option but it can be blocked if we send too much traffic to the SUPL servers. This would likely happen because /e/OS has a lot of users, and would have an impact in term of service continuity.
- Figure out how /e/OS users can use Advanced Privacy IP scrambling features to fake SUPL calls origin IP address.
- …?
You might want to try option 1 and check. Please revert back to this comment after attempting to do so, so that others can benefit from this idea.
XTRA uploads the following data types: a randomly generated unique ID, the chipset name and serial number, XTRA software version, the mobile country code and network code (allowing identification of country and wireless operator), the type of operating system and version, device make and model, the time since the last boot of the application processor and modem, and a list of our software on the device
They just forgot to mention that this data is sent with no encryption (except in the xtra3grc.bin format, hope that they’re exclusively using that now…). Of course it should be blocked. But it’s necessary to allow one of those 3 domains in order to make the GPS work properly.
And here’s the Wikipedia article on what is it that the Qualcomm chip is trying to gather: https://en.wikipedia.org/wiki/Assisted_GNSS
Thx for very detailed reply. I was trying to do the option 1, but I couldnt find how to do that.
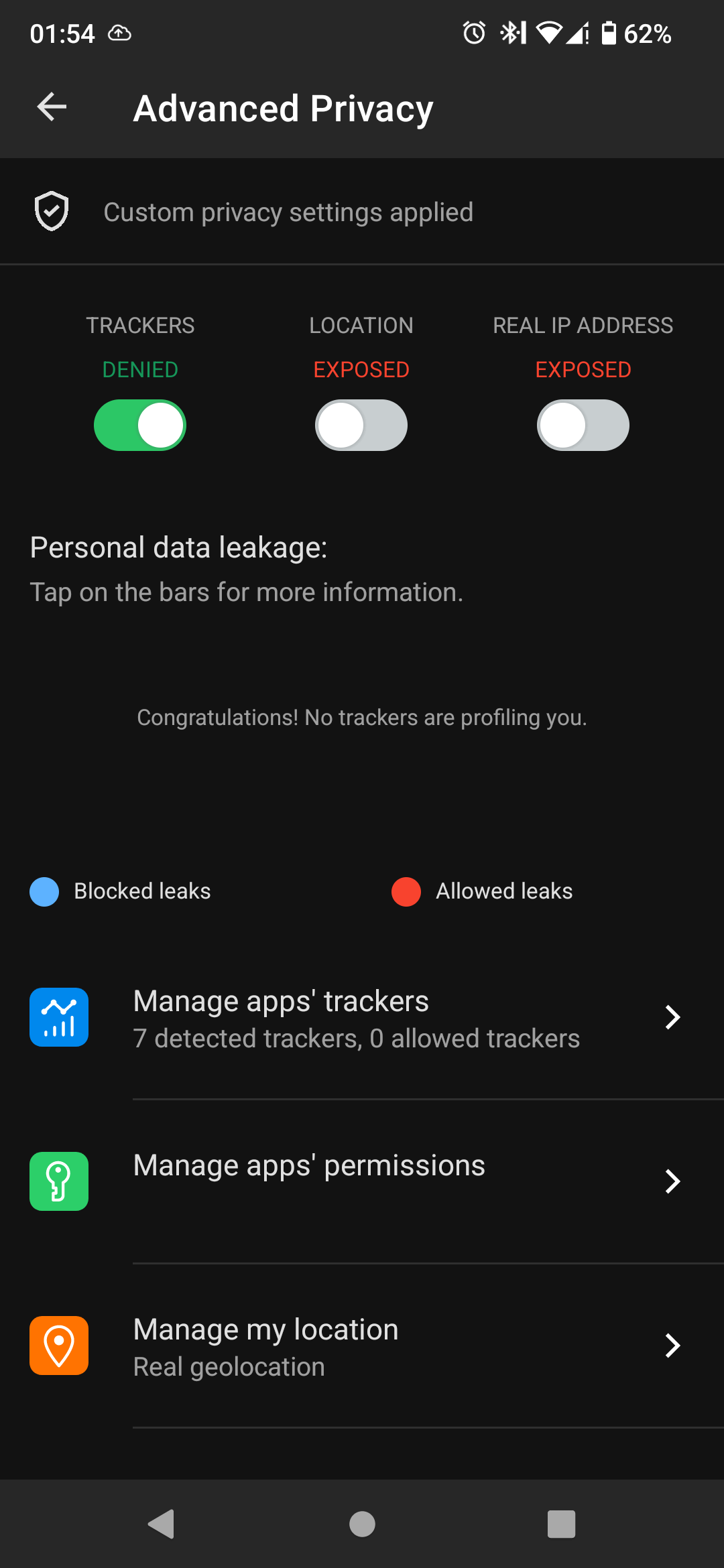
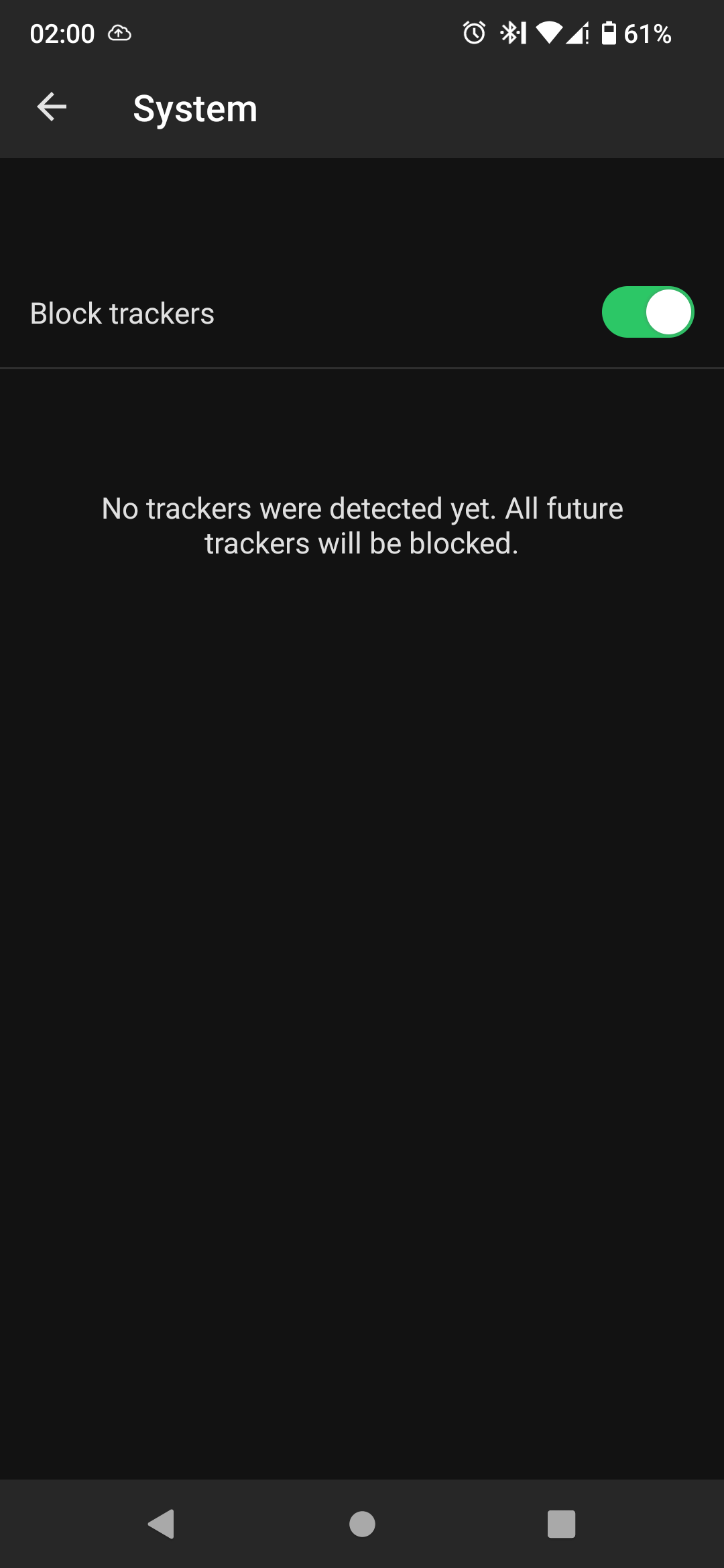
 I am guesing that because dns is blocking the requests they dont show in the app.
That would mean the app and dns are doing the same thing, so it doesnt really help.
I am guesing that because dns is blocking the requests they dont show in the app.
That would mean the app and dns are doing the same thing, so it doesnt really help.I might just allow them, because I need the gps to work properly.
I don’t have experience with e/OS/, I can only really say what I gather from their documentation.
Note that:
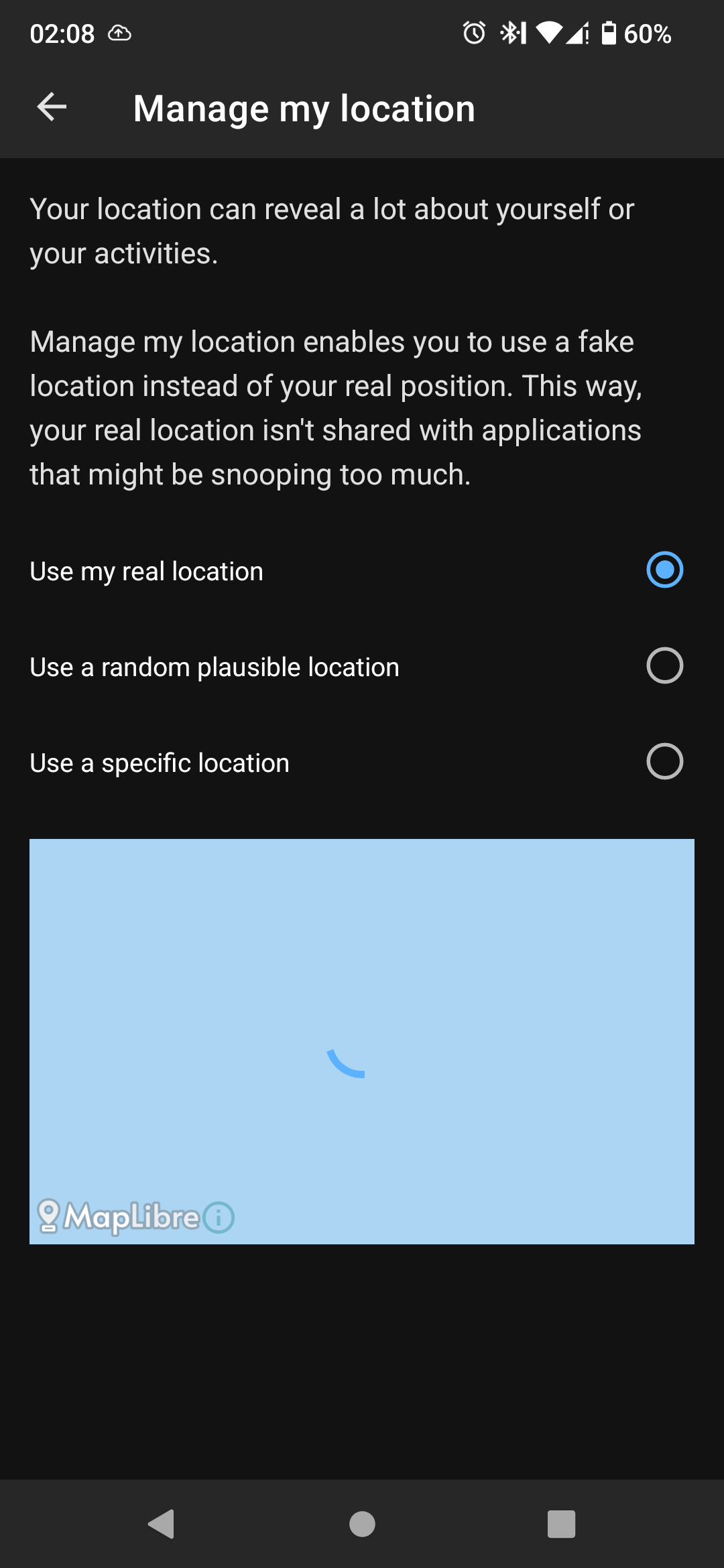
when I activate fake location in AP but keep location turned off in system settings the app organic maps does not show my fake location but asks me to enable location. Therefore I presume: Yes, location off in system settings means no location for any app.
The thing about modern android and location settings is that when it is turned off that also means the GPS. So probably correct, no location for any app.
Link to discussion: https://community.e.foundation/t/advance-privacy-fake-location-with-location-turned-off/50052
I would suggest utilising the Fake my location toggle for when you would not like apps to access your location, however, I am not sure if it will work against requests from low-level firmware such as directly from a Qualcomm chip. That’s a question for the developers.
Another point that is mentioned in this post is the fact that tracker detection and blocking (which is now native to e/OS/) can’t work with DoT providers like NextDNS. Indeed, the app and the DNS filters you’re using with your DNS provider attempt to do the same thing here.
Note that the “tracker manager” of Advanced Privacy can’t work with DNS over TLS (DoT).
I use location only for/with Organic Maps, otherwise it is turned off, so using fake location seems pointless.
It looks like if I want to use gps without problems I have to allow these connections. Or switch to pixel and GrapheneOS. Other chip makers like mediatek, samsung probably have something similar, so that isnt option either. I just got this FP4 and I like it alot, so I guess I’m stuck with qualcomm getting some telemetry.
Thank you very much for your help.
Just a heads up - Been following UT for some time and the major for me is that there is currently no VolTe support. Major bummer for US folks. There’s workarounds, at least for pixel3a but its not 100% reliable.
Also SMS / MMS can be troublesome as well. Can’t download images while on WiFi??? Group MMS doesn’t work.
Great system, works well but I can’t make it my daily driver
i tried it on my pixel 3a, its neat, and i can run android apps in waydroid, but I don’t like the navigation
deleted by creator
As far as I know it is still being developed.
deleted by creator
GrapheneOS really is the only Android that should be used. I hope e/OS and others just fork it, add a nicer UI and all.
- https://old.reddit.com/r/nextdns/comments/14919dp/randomly_pathnxtracloudnet_is_stopped_getting/jo5n5va/
The Qualcomm chipset is making these requests, most likely for GPS almanac data (satellite positioning).
Older chipsets send these almanac requests to izatcloud.net, unencrypted, containing your IMEI. No idea if newer chipsets have improved things though.
How do you deal with this? Or are you using iPhone or something else?
I don’t ☹️
There is a hidden LocationServices system app from Qualcomm that proxies the communication on some devices - however removing this causes a bootloop from what I’ve read, and would prevent Android from being able to identify your location even if it didn’t cause a bootloop.
I use a Fairphone 3 though with a bunch of Google services in the stock OS disabled, so I’ve settled for just keeping my location data out of Google’s hands
Edit: add info
Just decompile Qualcomm’s platform service and stub out the right system calls!
“Just”
You get pretty good at it after you do a couple. I also came up with a way to manually start a platform service with strace and a custom SELinux context, but that was a few years ago and I left all of that work with my previous employer.
I actually wanted to get a Fairphone 3 because of headphone jack but I got really good deal on a Fairphone 4 so I took it instead.
however removing this causes a bootloop from what I’ve read
Is this document for every Qualcomm device? I’d be interested to remove such calls from my system if possible, but I’m no systems expert, and unlike the other commenter I don’t think I’ll be able to decompile Qualcomm’s platform service just to remove a few system calls.
Chipsets don’t make network requests. More likely some closed-source platform service does.
That really isn’t entirely true anymore since the TPM ecosystem came into existence. I can remotely wipe any pc at my company even if it’s stolen and reformatted because a hardware chip will phone home the second a compatible os is installed and internet access is available.
The TPM can’t do anything. The Intel Management Engine and AMD Platform Security Processor can, but the TPM is just key storage.
That stuff is disabled unless you buy expensive business options, though. Intel makes a lot of money not putting the fancy smart stuff into their desktop platforms.
For remote wipe you also need to get lucky because if the thief doesn’t install the necessary drivers. Enabled encryption should prevent your company’s data from falling into the wrong hands, of course.
I think unless the HAP bit is specifically set to 1, Intel ME is still active on consumer boards, just without an interface for the OS to interact with it. Not sure if someone has hacked an OEM UEFI/BIOS to interact with it, but I have seen a different MAC address from my PC on my network before, and this is without any virtual adapters. This is the only explanation I can come up with.
The IME is active, but only for the bare necessities. Modern Intel CPUs simply will not bootstrap without the IME firmware. I know the thing runs Minix, but so far nobody who has reverse engineered it has found any serious threats when the management service isn’t running.
You can zero out some unnecessary components of the BIOS firmware so it can’t do networking and run daemons, but you need at least the ROMP and BUP partition.
Motherboard manufacturers can also toggle a bit that request the IME to be disabled after it finishes its critical initialisation code (I believe governments really like this feature) but you’d still be relying on Intel’s encrypted code. If you have a BIOS flasher (or a Raspberry Pi and some soldering skills or the right programming clip for your motherboard), you can make a backup of the BIOS and then enable the bit yourself.
I don’t know the source of your phantom MAC address. I’ve never seen an Intel ME DHCP request on my network. As far as I know, the Intel ME is supposed to take the same IP address as the host, unless you’re using a PCIe network adapter. The IME integrates with the Intel network card and extracts packets that it likes to operate on.
There is a Windows tool that will tell you your Intel ME MAC address if you want to confirm (MEInfoWin) if you want to confirm. It’s not a public tool that consumers are supposed to have access to, but you can find it (accidentally) distributed with firmware updates for motherboards.
Thanks for your comment, much appreciated! Could you provide a source for someone who has reverse-engineered a recent version of ME and has found not much incriminating behaviour for consumer motherboards?
Unfortunately,
me_cleanerdoesn’t seem to work too well with newer chips. Fortunately for me, I’m planning to purchase older computers, but for people who aren’t, this doesn’t help much (as far as I can see).Thank you for the idea of extracting the BIOS to enable the HAP bit. Won’t it require some serious reverse-engineering chops to find the HAP bit and enable it inside of such a binary blob? I’m not really used to Ghidra yet haha.
If I remember correctly, ME uses its own MAC address, but the same IP address of the host. Or maybe this is no longer the case. How would it extract packets though? Won’t that require serious compute power? Or does it look for packets with specific labels identifying them?
Thanks for letting me know about MEinfoWIN. I’ll try and find it!
Could you provide a source for someone who has reverse-engineered a recent version of ME and has found not much incriminating behaviour for consumer motherboards?
It’s hard to prove a negative, but with people doing deep dives like these not finding any malicious behaviour yet, I doubt there’s anything of note happening in the ME on consumer hardware.
Theoretically the NSA could backdoor the IME, but if they can backdoor the ME firmware, they can also backdoor the tiny Pentium processor inside every Intel CPU, or the UEFI ROM, the microcode, or any other firmware really. In practice they plant tiny their own chips onto existing motherboards, which can be easily removed so they don’t leave a trace.
Won’t it require some serious reverse-engineering chops to find the HAP bit and enable it inside of such a binary blob?
It looks like the HAP bit has changed location (someone already found out the new offset) but me_cleaner has built in support for setting the bit in many cases; this commit from this PR seems to implement that. Disabling the firmware does, as you would expect, disable the firmware loading process though, meaning Intel Audio won’t work right and booting becomes weirdly slow. You also lose fTPM support and modern sleep (S0ix).
How would it extract packets though? Won’t that require serious compute power? Or does it look for packets with specific labels identifying them?
The packets enter the Intel network card, and the network card pre-processes them in a bunch of ways (validating checksums, sometimes even reassembling fragmented frames). Modern network cards are fully aware of IP and in limited fashion TCP, so “extract traffic towards port 664/16993/16995 and do not notify the OS” isn’t that hard to accomplish.
A separate MAC with the same IP would cause tons of conflicts on the network, I don’t think Intel would (intentionally) use that approach.
For what it’s worth, I did specifically say ecosystem because the TPM is just one component, which is required to authenticate the remote wipe. Also the drivers are installed automatically with most modern operating systems, it’s not like you install your own south bridge driver, for example. Linux of course notwithstanding.
I’ve seen it used successfully numerous times. Someone steals one of our laptops, rips the drive out, installs vanilla windows, and boom it reboots and performs a wipe.
Regardless, system-on-a-chip are just that, systems; they can absolutely make remote calls without user interaction, just as intimated by the comment you originally replied to.
Ah, in that case I suspect this has less to do with the TPM or firmware and more with a weird feature Microsoft provides (that I permanently turned off on my laptop).
Windows provides the option for the BIOS to place or replace files on the file system. A bunch of anti-theft tools replace chkdsk.exe, which gets executed on every boot, with a daemon or installer for their service. You can clean install Windows all you want, the moment Windows boots, injection takes place and the payload gets executed. You don’t need TPMs or even encryption or Intel ME/AMD PSP for this.
I believe MS added this API because they noticed motherboard manufacturers messing with the kernel’s memory, and decided to expose a less batshit insane API rather than risk customers blaming Windows for their laptops crashing on boot because the memory layout changed.
Well, sounds like blocking them is bad: https://gitlab.com/CalyxOS/calyxos/-/issues/370
GPS almanac data.
/system/etc/gps.confand/system/vendor/etc/gps.confwill control how these connections work. There is a Magisk module that can override the config file, though you may need to edit the file to your liking, i.e. set the remote server to localhost.Disabling this will make GPS slow to get a fix, though. Basic GPS can take minutes to get a fix.
I use gps a lot, I don’t think turning it off is an option then, I will just have to allow it and live with this.
deleted by creator
Mix of both, depends where I am.
you can get calyx os for it (graphene isn’t supported)
Apparently calyx wouldn’t help. https://gitlab.com/CalyxOS/calyxos/-/issues/370
So fair 😇
I don’t really blame fairphone for this. They would probably have to make their own chips, if they wanted control over that. Almost nobody has money for that.
Naa that’s not something with “snapdragon cpu and location services” it’s something with snapdragon + the OS allowing it and most likely profiting from it. Fairphone guys have been petitioned multiples times to open their platform and/or collaborate with projects such as GrapheneOS and CalyxOS so user can have private and secure phones but they don’t care.
CalyxOS does support the Fairphone 4 however that’s only due to the persistence and reverse engineering efforts of the CalyxOS project / community. If you decide to use it you won’t have a secure bootloader anymore due to a bug in Fairphone’s firmware that they choose not to fix. That’s how “fair” the “Fairphone” really is.
Here is more relevant information for you from here:
XTRA is technology offered by Qualcomm Technologies, Inc. in the US and QT Technologies Ireland Limited in the European Economic Area to improve mobile device performance. XTRA downloads a data file from Qualcomm containing the predicted orbits of the Global Navigation Satellite System (GNSS) satellites. Using the XTRA data file reduces the time the device needs to calculate its location, thus saving time and battery power when using location-based applications. Newer versions of the XTRA software also upload a small amount of data to us. We use the uploaded data for purposes described in this Policy, such as maintaining and improving the quality, security, and integrity of the service. XTRA uploads the following data types: a randomly generated unique ID, the chipset name and serial number, XTRA software version, the mobile country code and network code (allowing identification of country and wireless operator), the type of operating system and version, device make and model, the time since the last boot of the application processor and modem, and a list of our software on the device
Before you say this is the CPU’s fault, it isn’t, at least on its own. GrapheneOS also deals with this kind of stuff and has patches and options so you can block it.
After looking into it more, I don’t think I would use Graphene OS even if it was supported on FP4, main dev seems like a lying man baby.
On the other hand, I didn’t know Calyx OS has support for FP4, I might try it out.
Why so much hate towards GrapheneOS? The thing is carefully planned and executed. About Calyx… just don’t forget that you won’t get a secure boot… anyone who gets you phone can temper with your boot.
I don’t hate GrapheneOS, it is probably fine. I just don’t think I would feel comfortable running an OS on my phone when its main dev acts like this. That’s just me and completely subjective.
Yes I’m aware of his bad soft skills… either way he does good work and he’s capable of working on small details while still seeing the bigger picture - this makes him able to spot and fix stuff others would miss easily. Example that stuff you’ve reported.
Wasn’t that the guy who stepped down from development entirely because of the backlash? Louis himself is still using it afaik
Here is an alternative Piped link(s):
https://www.piped.video/watch?v=Dx7CZ-2Bajg
https://www.piped.video/watch?v=4To-F6W1NT0
Piped is a privacy-respecting open-source alternative frontend to YouTube.
I’m open-source; check me out at GitHub.
I don’t really remember strcat “lying”, yet there are some evidence of him being… Let’s say unstable. GrapheneOS, tho, is another story as it’s trying to improve the android’s privacy/security model instead of simply not making things worse. For example, they are behind hardened malloc - for security, and have storage & contact scopes (i.e. letting the user choose which files/directories exactly an app can access) - for privacy. While the former feature has been adopted by a few other roms and even desktop Linux distributions, the latter I’ve seen only on graphene so far, which is quite a shame. Same goes for sandboxing play services
I bought the ancestor of GrapheneOS (CopperheadOS) for 500 bucks. I paid for two reasons:
- I wanted support
- I wanted the OS to be installed by the people behind the project, so that I could be certain it wasn’t tempered with, and didn’t have to rely on PKI, or PGP from random people. After all, it was meant to be secure. To that end, I even used a trusted courier.
Now AFAICT, the team back then was composed of two people: James Donaldson and Daniel Micay. James was the CEO and running operations, while Daniel was the CTO, and focusing on hardening.
Taking care of operations, James was the one who installed the software on my phone (I got confirmation of that fact from James himself). When I received it, it worked perfectly. It was great. I got to enjoy a nice, allegedly very secure OS for a few months.
Then, suddenly, after an OTA update, the microphone stopped working. The fact that it happened immediately after an update prompted me to believe that the OS update broke something.
I reported this to David Micay himself. To my surprise, he didn’t seem concerned at all, and refused outright to even take a look at the code changes in that update, without either having my phone or several MB of logs from the phone. In fact, he strongly implied it must have been user error (i.e. my fault), or hardware failure (i.e. Google’s fault).
The possibility of he himself having introduced a bug, or of his stack having produced a partially failed build, seemed absolutely inconceivable to him.It was necessarily someone else’s fault.
Neither option was acceptable to me. I wasn’t about to pay for another courier, especially to send a product to be processed without any guarantees, to someone who obviously didn’t give the tiniest fuck; and I surely wasn’t going to send several megabytes of personal, confidential information, to someone who just flat out insulted me, and arrogantly implied that the Google hardware would likely fail sooner than his software (fun fact, that “Google hardware sucks” phone still perfectly works today).
So, instead, I immediately bought another phone, installed lineage on it, and that other phone still works perfectly to this day (microphone included!). Albeit with a pretty weak battery.
Unsurprisingly, some months later, David was canned from the CopperheadOS project. However, to my horror, he destroyed the signing keys in the process. So there was then no way anymore of eventually getting a fix for his bug (I was hoping that, at some point, knowingly or not, he would somehow introduce a change that would fix the bug. After all, this is how the bug first occurred, so it wasn’t unreasonable to hope it could also be how it would be fixed, given that no other fix would happen).
Therefore, the very expensive license was useless to me. I really wish James would have re-signed the software during deployment, and made updates available signed with that same key, therefore preventing David from destroying the entire value of all sales.
Indeed, said keys could only be trusted if the install had been done by CopperheadOS Ltd (and if the device was kept by a trusted supervisor at all times after). In any other case, there could have been tampering, since the bootloader had to remain unlocked.
And leaving the keys with the Ltd was the semantically correct thing to do, for all intents and purposes:- If James was so untrusted that the keys would have to be destroyed upon David leaving, he would have been untrusted before too, so letting James run all operations would have been a grave security oversight.
- If James wasn’t untrusted, keys could have been transferred securely, or replaced via an update.
So, pretending to have destroyed the keys “To EnShUeH sEcUrItEh!!!1” was quite clearly a fallacious reason.
What evidently happened is that David was butthurt, sought revenge, and didn’t give the slightest fuck about the damage to other people.I kept my CopperheadOS phone as a reminder never to trust this dev again. Never to trust anything he has control over. Never to trust any company he works for.
And I salute your indubitably pertinent judgment. I wish I had had the same wisdom, I would have saved a bunch of money in not buying the most expensive paperweight I have ever bought.
Thanks, that was interesting and eye opening read. Do you know if he is still working on graphene os or is he out? Because some users mentioned that he left.
I actually paid negative attention to GrapheneOS. By that I mean actively avoided it. So I wouldn’t know.
Removed by mod
Oh man, you seem lost. Do you need help? Did you take a wrong turn when looking for c/boobs?








